Skip the manual plugin installation with no-code Backstage
Request a Roadie demo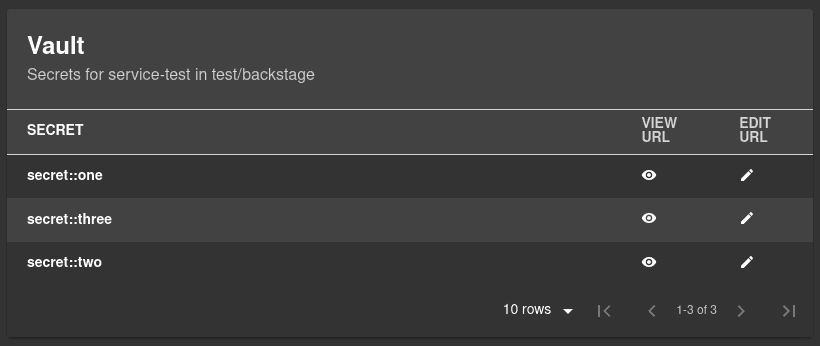
Installation steps
Install the front-end plugin.
cd packages/app
yarn add @backstage/plugin-vaultAdd the Vault card to the entity page.
// packages/app/src/components/catalog/EntityPage.tsx
import { EntityVaultCard } from '@backstage/plugin-vault';
const overviewContent = (
<Grid container spacing={3} alignItems="stretch">
{/* ...other content */}
<Grid item md={6} xs={12}>
<EntityVaultCard />
</Grid>
);Get a VAULT_TOKEN with LIST capabilities and add it to app-config.yaml.
# app-config.yaml
vault:
baseUrl: http://your-vault-url
token: <<VAULT_TOKEN>>
secretEngine: 'customSecretEngine' # Optional. Default: 'secrets'
kvVersion: <<kv-version>> # Optional. The available options are '1' or '2'Found a mistake? Update these instructions.
Things to know
Including secrets in the Catalog
The Hashicorp Vault plugin for Backstage allows you to include secrets as part of your Catalog’s components. You’ll have to add the Vault’s path to your secrets relevant to each component in their respective catalog-info.yaml.
For instance, for my ReallyCool component, which stores secrets in Vault’s secrets/path/to/really-cool, then I need to set an annotation like this:
apiVersion: backstage.io/v1alpha1
kind: Component
metadata:
# ...
annotations:
vault.io/secrets-path: path/to/really-coolAs you can see, the path you specify here is be relative to what you set as secretEngine in app-config.yaml.
Token requirements
This Backstage plugin needs a Vault token to be able to access a list of secrets URLs. The plugin only needs LIST capabilities.
The plugin also comes with an auto-renewal option, to enable it, include self-renewal capabilities in your token’s custom policy:
# Allows token to renew itself
path "auth/token/renew-self" {
capabilities = ["update"]
}For more information, consult Vault’s documentation.
Prefer a no-code Backstage setup?
Request a Roadie demoBecome a Backstage expert
To get the latest news, deep dives into Backstage features, and a roundup of recent open-source action, sign up for Roadie's Backstage Weekly. See recent editions.
